Update February 17, 2022: A second patch was released which must be applied over the first one. I added instructions on how to apply that at the end of this blog post.
On February 13, 2022, Adobe released a critical security patch named "APSB22-12" for all recent versions of Magento Open Source and Adobe Commerce.
The security issue allows to execute arbitrary code on the Magento server - no admin access needed. It was assigned the highest priority by Adobe.
How to apply the patch - the (too) easy way
Adobe has also published a patch file and instructions on how to apply it, see this link to the Adobe Help Center.
If you are using Adobe Commerce Cloud (formerly Magento Cloud), it's pretty easy: You put the patch file into the directory "m2-hotfixes" and run the integrated deployment process.
For other hosting solution, Adobe tells us to apply the patch on the command line:
patch -p1 < %patch_name%.composer.patch
The problem: This doesn't work well with continuous integration as this command and the file have to be added to the deployment pipeline.
There is a solution for that though.
How to apply the patch - the composer way
This way includes applying the patch via composer which is used by Magento anyway. If done correctly, the patch will be applied every time a composer command like "composer install" is called. Typically, this is already done by the deployment pipeline, there will be no need to adjust it.
The solution consists of three parts:
1. A composer plugin
You add the composer plugin with this command:
composer require cweagans/composer-patches
With this, the "Composer Patches" plugin by Cameron Eagans is installed. It allows to apply patch files automatically.
2. Slightly modified patch file(s)
The patch file which is delivered by Adobe needs some small changes with the directory paths because the "Composer Patches" plugin applies them per repository instead of globally.
So, we need to split the patch file to one file per repository which is affected - in this case, we need one for magento/framework and one for magento/module-email. Then, the paths inside the files have to be adjusted so they don't contain the "vendor/magento/framework/" or "vendor/magento/module-email" part any more.
I have prepared the modified patch files for you so you can just download them here.
The patch files should be added to a new "patches" subdirectory to your Magento repository so it looks like this:
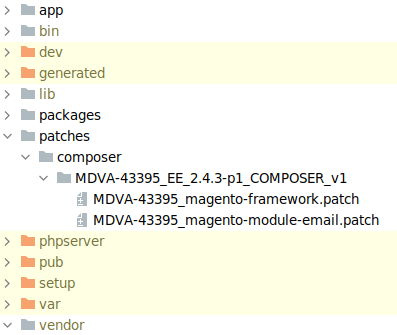
3. Modifications to composer.json
We need to add a few new lines to the "extra" part of our project's composer.json file:
"extra": {
[...]
"composer-exit-on-patch-failure": true,
"patches": {
"magento/framework": {
"MDVA-43395": "patches/composer/MDVA-43395_EE_2.4.3-p1_COMPOSER_v1/MDVA-43395_magento-framework.patch"
},
"magento/module-email": {
"MDVA-43395": "patches/composer/MDVA-43395_EE_2.4.3-p1_COMPOSER_v1/MDVA-43395_magento-module-email.patch"
}
}
},
"magento/framework" and "magento/module-email" are the repositories to which the patch files should be applied. It is followed by an identifier "MDVA-43395" and the full path to the patch file.
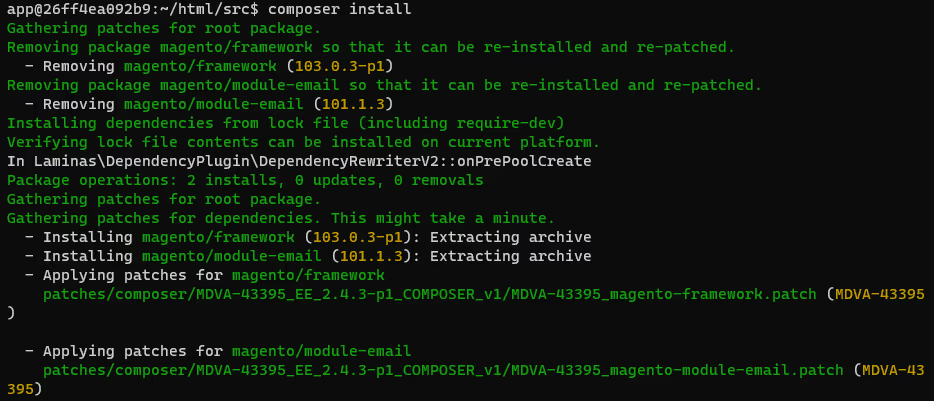
Now you call "composer install" and the patches are applied automatically.
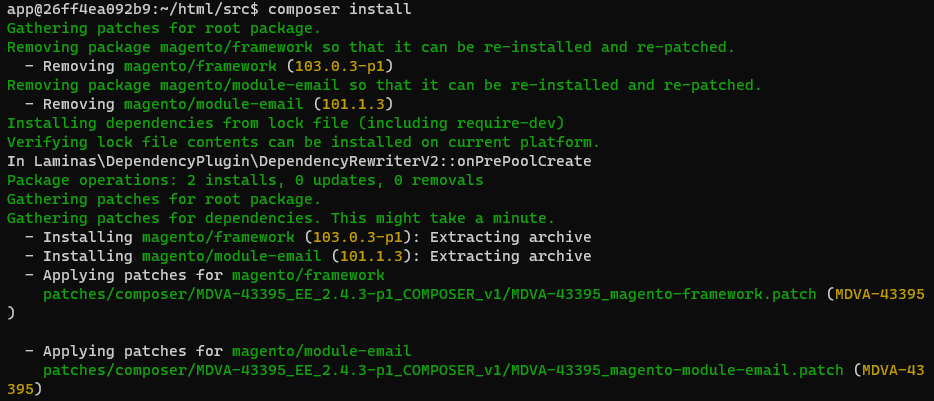
Optional: This composer command updates the composer.lock file's hash sum so it doesn't appear as outdated:
composer update --lock
Let's see what changes the patch file brings to one of the affected files.
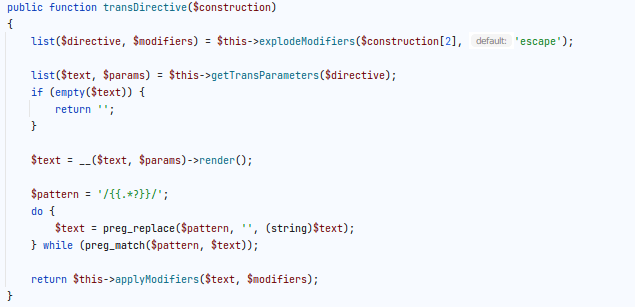
Before applying the patch to vendor/magento/module-email/Model/Template/Filter.php:
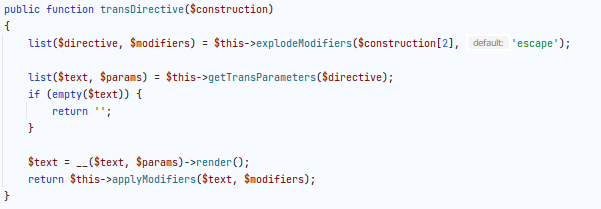
After applying the patch to vendor/magento/module-email/Model/Template/Filter.php:
And that's it! I hope this makes it easier for you to apply this critical patch in your Magento Open Source or Adobe Commerce systems.
Update February 18 2022: A second patch
The Adobe security bulletin was updated on the evening of February 17th with a second patch as the first patch still left an attack vector open.
The process to apply it is the same as for the first patch.
The new part in the composer.json should look like this:
"extra": {
[...]
"composer-exit-on-patch-failure": true,
"patches": {
"magento/framework": {
"MDVA-43395": "patches/composer/MDVA-43395_EE_2.4.3-p1_COMPOSER_v1/MDVA-43395_magento-framework.patch",
"MDVA-43443": "patches/composer/MDVA-43443_EE_2.4.3-p1_COMPOSER_v1/MDVA-43443_magento-framework.patch"
},
"magento/module-email": {
"MDVA-43395": "patches/composer/MDVA-43395_EE_2.4.3-p1_COMPOSER_v1/MDVA-43395_magento-module-email.patch",
"MDVA-43443": "patches/composer/MDVA-43443_EE_2.4.3-p1_COMPOSER_v1/MDVA-43443_magento-module-email.patch"
}
}
},
We have also updated the new patch file, split it in two and adjusted the paths. You can download the updated patch files here.
Please note that these files will only work if you are using Magento 2.4.3. Adobe has provided different patch files for older versions in its security bulletin.